
The Centre for the New Midlands are proud partners of a new research project, being led by the University of Nottingham, focussed on enhancing Cyber Resilience of Small and Medium Sized Enterprises (SMEs) through Cyber Security Communities of Support (CyCOS).
In this article, Professor Steven Furnell (Professor of Cyber Security, University of Nottingham and Cyber Security Lead, Centre for the New Midlands) introduces the project and outlines the ways in which SMEs can engage in the initiative. With special thanks to project team members Neeshé Khan, Maria Bada and Jason Nurse for co-authoring this article.
(March 2024)
Cyber security remains a key priority for organisations of all sizes, and a prior article has explored our position in the Midlands in terms of possessing the skills to address the requisite needs. While ensuring appropriate protection is not an issue for everyone, it is typically a more challenging prospect for Small and Medium-sized Enterprises (SMEs), with less capability and resources to address it (in terms of both in-house expertise and budget to invest or engage externally).
The 2023 release of the UK’s Cyber Security Breaches Survey showed a notable decline in SMEs following basic cyber hygiene practices, such as the use of password policies, network firewalls, and ensuring the timely application of security updates. The decrease was particularly amongst micro businesses, and may be indicative of attention towards security being sacrificed in the face of post-pandemic economic challenges. However, while shifting priorities can be expected, the consequence for the businesses concerned could nonetheless be unfortunate. Most cyber attacks are opportunistic and based around techniques that basic hygiene measures will help to thwart. Given that SMEs account for a huge proportion of the UK economy, having a greater proportion of them being left potentially exposed is not good news.
Of course, one of the challenges for most SMEs is that they have relatively limited understanding about what cyber security involves. While good resources are available to help, SMEs may not be aware of them and may not know how to put the advice into practice. For example, the Cyber Security Breaches Survey reports that only 15% of micro and small businesses have heard of the NCSC’s Small Business Guide.
The CyCOS project
The above concerns have led to the establishment of the CyCOS research project, which aims to enhance the cyber resilience of SMEs by offering a new means to access support around cyber security, and to share lessons and experiences from their peer community. The project is being undertaken by the authors, in collaboration with a range of relevant supporting partners including the UK Home Office, IASME, ISC2, the Chartered Institute for Information Security, three regional Cyber Resilience Centres, and the Centre for the New Midlands.
The 30-month project began in September 2023 and is currently in the phase of collecting data about SMEs’ needs, their use and perceptions of the cyber security support that is currently available, and the challenges they may face. This includes data collection from both SMEs and various existing sources that already provide advice and guidance. Beyond this, the work aims toward the establishment of new Cyber Security Communities of Support, offering an additional (and complementary) means by which SMEs can engage with cyber security and seek support from a community of peers and advisors. Such communities may operate on a local basis, as well as amongst SMEs based in the same sector, and the project will run a series of pilot activities in order to evaluate the effectiveness of the approach.
Evaluating guidance from online sources
Early work within the project has sought to examine the support that SMEs can already find available to them. One of the aspects of this has been to assess the guidance that can be found online, which is likely to be a natural starting point for many SMEs seeking to understand what they need to know and what to do. A series of related sources were identified by means of web search for SME-facing guidance, or by directly visiting sites from providers that SMEs would be expected to know and potentially view as authoritative and credible (e.g. official sources, Internet Service Providers). After filtering, this left a set of 31 relevant sources, each offering information directly identifiable as a small business cyber security guide (or offering ‘top tips’, ‘key advice’ or similar). However, an evaluation of the resulting materials (assessing the coverage, clarity and completeness of each source) revealed that the guidance provided was anything but consistent.
The table below presents a subset of the findings, taking two sources from each of the provider categories as examples. In each case, the table is indicating whether the guidance included coverage that could be mapped to each of the NCSC’s 10 Steps to Cyber Security, as well as whether there was coverage to explain the nature of SME-facing cyber threats more generally. As can clearly be seen, there is a wide variation in what each source is found to cover, and some topic areas tend to receive scant coverage compared to others. Against this backdrop, it would be entirely reasonable to find SMEs coming away with an incomplete and inconsistent information, and thereby potentially remaining confused about what they should actually be doing.
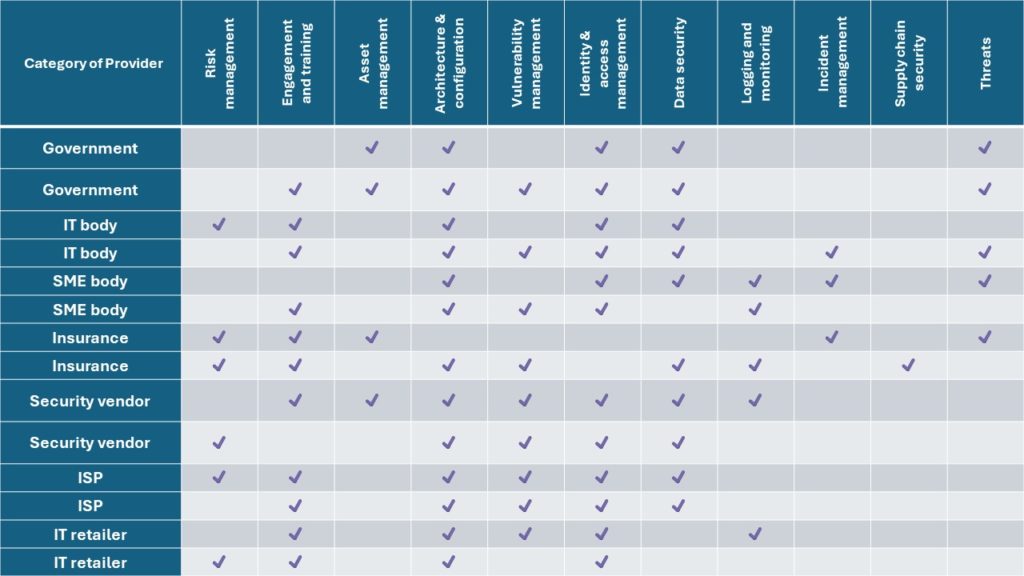
The clarity and completeness factors were also significantly variable. In terms of clarity, the majority did not define ‘cyber security’ and half provided steps that were considered difficult to follow. In terms of completeness, a little over a third only offered topic-level advice whilst the length of the guide itself varied across the board. Our assessment therefore suggests that SMEs may find the materials relatively limited, and (despite the naming of various sources referring to offering guides and tips) typically of more use in raising awareness than guiding resulting actions.
Getting involved
Beyond the assessment of the online sources, the project is also conducting interviews with various organisations that provide advice and support to SMEs, as well as conducting survey and interview-based data collection from SMEs themselves in order to determine their perspective on current support and challenges. Anyone SMEs interested in completing the survey for this aspect is welcome to do so via https://app.onlinesurveys.jisc.ac.uk/s/qmul/cycos.
Beyond this, the project is undertaking further activities to track SME support journeys as they unfold, in order to develop case studies of what works and how to avoid issues. We are also keen to hear from SMEs or advisors that would be interested in joining the future communities of support.
You can find out further details of the project at www.cycos.org and get in touch with the project team via contact@cycos.org.
Project Team Members:
Steven Furnell, Professor of Cyber Security, University of Nottingham and Cyber Security Lead, Centre for the New Midlands)
Neeshé Khan, Research Fellow in Cyber Security, University of Nottingham
Maria Bada, Lecturer in Psychology, Queen Mary University of London
Jason Nurse, Reader in Cyber Security, University of Kent
ABOUT OUR AUTHOR:
Professor Steven Furnell is a Professor of Cyber Security at the University of Nottingham in the United Kingdom. He is also an Adjunct Professor with Edith Cowan University in Western Australia and an Honorary Professor with Nelson Mandela University in South Africa.
His research interests include usability of security and privacy, security management and culture, and technologies for user authentication and intrusion detection. He has authored over 350 papers in refereed international journals and conference proceedings, as well as various books, book chapters and industry reports.
Steven is the UK representative to Technical Committee 11 (security and privacy) within the International Federation for Information Processing, as well as the editor-in-chief of Information and Computer Security, and a Fellow and board member of the Chartered Institute of Information Security.
